BACK
Cryptography: Cryptography,
EFS (Encrypting File System), IPSec
See also the Authentication section
elsewhere in this site
Cryptography
High level view of cryptography:
CLEARTEXT --> encrypt --> CIPHERTEXT --> de-crypt -->
CLEARTEXT
Design goals of cryptology
- Confidentiality
- Integrity
- Non-repudiation
- Authentication
Uses of cryptology
- Encrypting email and files
- Signing email and files
- SSL
- IPSec
Symmetric
- two way
- private key encryption
- fast
- Ex.: ROT13 uses the same algorithm and key to both encrypt and decrypt:
move forward 13 letters in the alphabet, wrap around from z to a. This is
a non-standard example as usually the algorithm is reversed between encryption
and decryption
Asymmetric
- one way
- uses a key pair
- public key encryption (PKI)
- slow for large tasks
Hash
- One way encryption
- Special summery (Any one source will always hash to the same hash, but also
two different source can potentially hash to the same hash.)
- A lossy non-reversible predictable process
- Ex.: rip a high quality CD track to a low quality .mp3 file. Do it twice
with the same settings, software, hardware, etc., and the two mp3s could be
identical. With cryptographic hashes two hashes of the same source done with
the same hash will be identical. Now try to convert the .mp3 file back to
a high quality raw file which is identical to the original CD - can't do it.
The hash (.mp3) is significantly smaller than the source (.wav).
Signing = sender’s message is hashed and then the sender’s private
key used to encrypt this hash, the encrypted hash is the signature. The receiver
decrypts the signature using the sender’s public key back to the hash,
independently hashes the message, and compares the two together – if they
are the same the message is indeed signed by the private key holder and has
not been changed in transit. Note that the message was readable in transit by
third parties.
Encrypting = sender’s message is encrypted with receiver’s public
key. Receiver decrypts encrypted message with their own private key. Only the
intended receiver can decrypt. The message was not readable in transit at all.
Symmetric = two way = private key encryption = fast
Asymmetric = one way = uses a key pair = public key encryption
(PKI) = slow for large tasks
FIPS (Federal Information Processing Standard) activation forces:
- SHA-1 for hashing
- 3DES for TLS and EFS
- RSA for TLS public key exchange
Encrypting File System - EFS
Reference ISBN: 0321305019 Roberta Bragg's "Windows Server 2003 Security
: A Technical Reference" for great detail.
Encrypting File System (EFS) OS >= 2000:
- EFS on by default
- feature of NTFS - files or folders can be encrypted -
process is transparent to user
- RSA is PKI algorithm
- can't encrypt system root or files with system attribute set
- data recovery is by file recovery
- esfinfo utility shows encryptor (sp?) and recovery agent
Encrypting File System (EFS) OS >= XP, all of above plus:
- shared use!
- recovery agent NOT required
- works with offline files
- cli key export
- stronger algorithms
- data recovery is by key recovery when with AD CA
- able to use over WebDEV
- advanced properties shows encryptor and recovery agent
key archival: 2003 CA has ability to archive user's private EFS keys
Standalone systems operate differently from domain based...
| Algorithm choices by OS, bold is default |
| 2000 |
DESX |
| XP |
DESX, can use 3DES |
| XP SP1 |
DESX, 3DES, AES |
| 2003 |
DESX, 3DES, AES |
Certificates and keys must be backed up and secured as part of the EFS use
and data recovery policy.
Private key should be removed from the system to greatly reduce attacker's
ability to unencrypt encrypted files - however, with the private key removed,
even the authorized user (username and password) can't unencrypt.
Layers of protection:
- user's certificate and private key are stored in user's profile - protected
by master key
- master key based on user's password
- master key encrypted when not in use
- administrator forced password change on a standalone machine breaks the
password master key link and renders EFS encrypted files un-unencryptable!
Undo with password reset floppy disk.
EFS GPO settings are in Windows Settings / Security Settings / Public Key
Policies
NTBACKUP supports backing up encrypted files.
EFS encryption steps:
- NTFS driver calls fsclient which calls either local or remote LSA (Local
Security Authority)
- LSA checks rights and free space
- LSA generates FEK (File Encryption Key) - each file gets an new FEK
- LSA encrypts FEK with user's and recovery agent's public key
- LSA writes EFS metadata including: version, algorithm used, DDF (Data Decryption
Fields), DRF (Data Recovery Fields)
- Each DRF is the FEK encrypted with a user's public key (the DRF maxes at
256K ~800 users per file)
- LSA encrypts file with FEK
- This process is a performance optimizing mix of private and public encryptions
cipher cli:
- /e = encrypt
- /d = decrypt
- no switch = list encrypted
- /x = export keys
- /w = wipe data shreds
Third-party certification authority support for encrypting file
system
http://support.microsoft.com/?kbid=273856
File servers:
- Files on EFS shares, when connected to via SMB, transit the network in the
clear
- For EFS to function via SMB on a file server roaming profiles work best,
second to that the file server must be trusted for delegation
- WebDEV shares (run by IIS) encrypt on the local client, files transit the
network encrypted
IPSec
IPsec is a suite of protocols for securing IP communications by authenticating
and/or encrypting each IP packet in a data stream.
<opinion> The Internet is powerful and grew and is growing and TCP/IP
is the de facto network operating system due to its open-ness and focus on network
intelligence at the edge instead of the core. With the use of the Internet by
business and increased ease and return on cracking [malevolent hacking] IPSec
offers security enhancements to a basically naked TCP/IP stack. </opinion>
IPSec is built natively into IPv6, but is an add-on to IPv4. IPSec uses IKE,
AH, and ESP.
Note about the default supplied with the OS client, server,
and secure server IPSec policies: Depending on your reference source,
these are usually categorized as samples for learning and lab work only, all
the way to other sources saying these three are all you'll probably ever need.
DEFINITIONS:
- AD - Microsoft Active Directory. A proprietary
directory service and network operating system
- AH - Authentication Header. AH is a protocol used for authenticating
a data stream. It uses a cryptographic hash function to produce a MAC from
the data in the IP packet. This MAC is then transmitted with the packet, allowing
the remote gateway to verify the integrity of the original IP packet, making
sure the data has not been tampered with on its way through the Internet.
- ESP - Encapsulating Security Payload. The ESP protocol
is used for both encryption and authentication of the IP packet. It can also
be used to do either encryption only, or authentication only.
- Gateway - congregation point on the network through which
to jump from one network or protocol to another
- GPO - AD Group Policy Object. In the context
of IPSec this is a group of IPSec polices linked (applied) to a bunch of hosts
(via OU, for ex.)
- Host - a device on the network (LAN or WAN), ex. server,
workstation, etc.
- IKE - Internet Key Exchange. Provides a means for the
endpoints to authenticate each other. Establish new IPsec connections (create
SA pairs). Manage existing connections. (IKE receives authentication
and security settings from the Policy Agent and waits for requests to negotiate
IPSec SAs. When requested by the IPSec driver, IKE negotiates both kinds of
SAs (main mode and quick mode) with the appropriate endpoint requested by
the IPSec driver based on the policy settings obtained from the Policy Agent.
After negotiating an IPSec SA, IKE sends the SA settings to the IPSec driver.)
- IP - Internet Protocol
- IPSec - Internet Protocol Security
- ISAKMP - Internet Security Association and Key Management Protocol
- Kerberos - a network authentication protocol designed to
provide strong authentication for client/server applications by using secret-key
cryptography.
- NAT - Network Address Translation. Deployed to allow more
IP addresses to exist and/or to create private IP networks with Internet connections.
- NAT-T - NAT-Traversal
- NDIS - Network Driver Interface Specification
- NIC - Network Interface Connection/Card.
- SA - Security Association
- TCP - Transport Control Protocol. A so-called reliable
transport layer protocol.
- UDP - User Datagram. A so-called un-reliable transport
layer protocol.
Major points on this protocol:
- IPSec uses cryptography-based security to provide access control, connectionless
integrity, data origin authentication, protection against replays and spoofing,
confidentiality, and limited traffic- flow confidentiality.
- Because IPSec is provided at the IP layer, its services are available to
the upper-layer protocols in the stack and, transparently, to existing applications.
- IPSec authenticates endpoint devices - NOT users. Mutual device
authentication.
- IPSec establishes and maintains cryptographic keys for each security relationship.
- IPSec can protect a path between two hosts or, a path between two security
gateways, or a path between a host and security gateway. Note that each host
can simultaneously have multiple IPSec connections in use/established.
- IPSec policy may be configured locally on a computer or can be assigned
through Windows 200x Group Policy .
- When using the Active Directory, hosts detect policy assignment at GPO application
(startup), retrieve and apply the policy, and then are periodically updated.
- IPSec can use either certificates or Kerberos or a pre-shared key as the
authentication method.
- Each IP datagram processed at the IP layer is compared to a set of filters
that are provided by the security policy. The TCP/IP stack either: (1) provides
IPSec services to it, (2) allows it to pass unmodified, or (3) discards it.
- An IPSec policy contains a filter, filter action, authentication,
tunnel setting, and connection type.
- A SA is established through a short ISAKMP conversation over UDP
port 500, through IKE (this is the main mode part), and then
the traffic begins to flow.
- Actual traffic flow, encapsulated by IPSec (this is the quick mode
part) is via AH using IP protocol number 51, and ESP
using IP protocol number 50.
- The ESP extension header provides origin authenticity, integrity, and confidentiality
protection of a packet. ESP also supports encryption-only and authentication-only
configurations, but using encryption without authentication is strongly discouraged.
Unlike the AH header, the IP packet header is not accounted for. ESP operates
directly on top of IP using IP protocol number 50.
- The AH is intended to guarantee connectionless integrity and data origin
authentication of IP datagrams, and protect against replay attacks. AH protects
the IP payload and all header fields of an IP datagram except for mutable
fields (those that might be altered in transit): TOS, Flags, Fragment Offset,
TTL and Header Checksum. AH operates directly on top of IP using IP protocol
number 51.
- Using a secure server policy also restricts (denies) all other types of
traffic from reaching destinations that do not understand IPSec or are not
part of the same trusted group.
- When IPSec is used to encrypt data, network performance generally drops,
due to the processing overhead of encryption. One possible method for reducing
the impact of this overhead is to offload the processing to a hardware device.
Because NDIS 5.0 supports task offloading, it is feasible to include encryption
hardware on NICs.
- IPSec has trouble with NAT (NAT-T resolves some of this)
- Oakley logs track the establishment of SAs. This type of logging is not
enabled by default and must be enabled with the command “netsh ipsec
dynamic set config ikelogging 1”.
IPSec tools:
- IP Security Monitor snap-in (Windows 2003 / XP)
- ipseccmd (Windows 2000)
- netsh ipsec
- Windows Network Monitor (or any sniffer) can see IPSec traffic BUT CAN NOT
SEE INTO IT. So for looking at presence and sizes and from where to where
it is okay troubleshooting-wise, but sniffer use is very limited otherwise.
(This is true for firewall and IDS devices allowing IPSec through too.)
- The Routing and Remote Access snap-in can be used to view the VPN connections,
but it cannot monitor the IPSec security associations.
- The Performance Monitor does not have a counters for IPSec.
The term mode is overused, you need to choose:
- Either AH mode or ESP mode (or both) AND
-
| AH mode |
Authentication |
| ESP mode |
Authentication and/or Encryption |
- Either transport mode or tunnel mode AND
-
| Transport mode |
Point to point IPSec |
| Tunnel mode |
Router model |
- Successful IPSec communications goes through both first main mode and then
quick mode
-
| Main mode |
Negotiation stage - sets up SAs |
| Quick mode |
Actual traffic flow |
Anatomy of IPSec.doc - a "Down
in the weeds" look at MS IPSec
IPSEC_FAQ.ppt - Largish MS Power Point on
IPSec - A MS KS article simply turned into a ppt...
AH Transport Mode Packet Structure: 
ESP Transport Mode Packet Structure: 
AH Tunnel Mode Packet Structure: 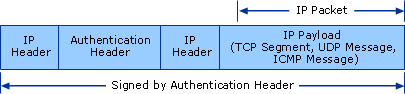
ESP Tunnel Mode Packet Structure: 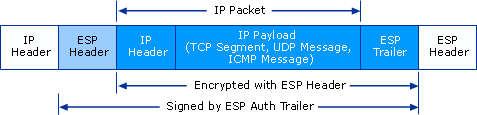
Certificate Services
"Certificate Services" is Microsoft's PKI (Public Key
Infrastructure) implementation
Certificates
- Name
- SN
- Valid from and to dates and times
- Contain users public key (PKI)
- Signed with CA servers' signature
CA - Certificate Authority
- Issues certificates
- Issues CRL
- IE hosts a list of trusted CA roots
- Run your own CA for reduced certificate cost and to retain control
- Use third party CA to provide access to clients over the 'net
CRL - Certificate Revocation List
- Delta CRLs are a new 2003 feature
Certificate enabled applications
- Email
- Web browsing
- OS - smartcards
MISC
FIPS (Federal Information Processing Standard)
activation forces:
- SHA-1 for hashing
- 3DES for TLS and EFS
- RSA for TLS public key exchange
Cryptography Decrypted
by H. X. Mel, Doris M. Baker, Steve Burnett
ISBN: 0-2016-1647-5
$37.99
A little dry, but thorough. Maybe out of date by now too...
BACK




